Bug Bounty (wikipedia)
A bug bounty program is a deal offered by many website and software developers by which individuals can receive recognition and compensation for reporting bugs, especially those pertaining to exploits and vulnerabilities.
Bug Bounty Guide:
- Learn and study all types of common attack like XSS, SQL Injection, RFI, LFI and others. Remember one thing that hacking and vulnerability assessment are not same. To be a good bug bounty hunter you must know, how a vulnerability is generate and what is the wrong in coding to generate a vulnerability. It helps you mentally to find out where maybe the vulnerabilities are exist.
- Find out which companies or websites are under bug bounty program. Searching in Google you can get a list of them. ex: Bug Bounty Program websites .
- Using vulnerability assessment tools or any vulnerability scanner is not a good idea to become a good bug bounty hunter. You should use your brain not any software.
- If your target is any big website than try to find out the sub domains of that website. It will be more easier to vulnerability assessment over it. But before that you should read their terms and conditions to know that is sub domains are allowed in bug bounty or not.
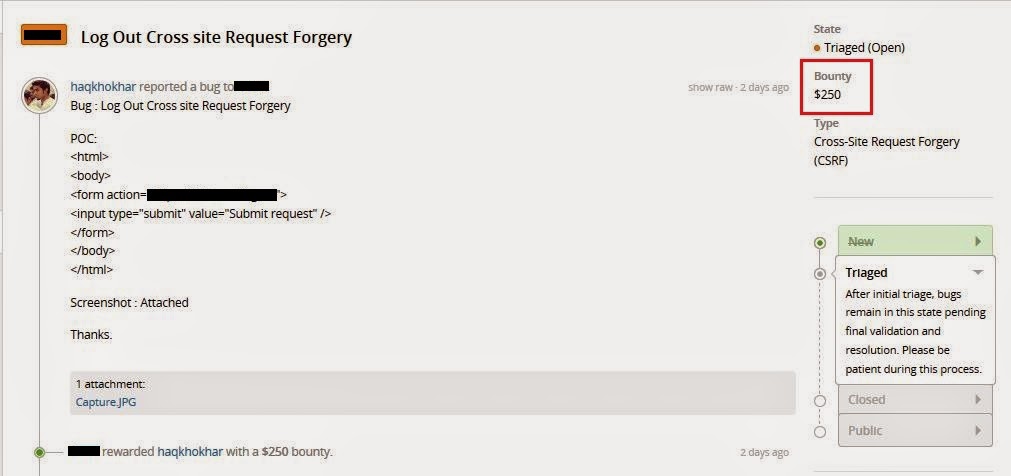
- After your vulnerability assessment make a details report with POC about that vulnerabilities you have found. On your report you must highlight what kind vulnerability is about and what is the negative impact of that vulnerability if it found by any offensive hacker.
- After submitting your report wait for the replay. If you disclosure the vulnerability before their replay it is not good for your reputation
Thanks for Reading this Article and if you need any information so feel free to comment below .